It’s been just over a year since the introduction of Public Good Staking, and in this time, more than 20 blockchain protocols have adopted it. This includes everything from the largest blockchain ecosystems to startup protocols.
Public Good Staking essentially involves allocating a portion of a blockchain network’s incentives to fund innovative ideas and developers' activities, all without compromising the network’s protocol security. For Proof of Stake (PoS) networks, adopting Public Good Staking can offer long-term benefits by providing sustained funding to developers and the broader ecosystem. Given the current rate of adoption, we are poised to transform the way PoS ecosystems fund hackers’ projects and ventures over time.
When we take a broader view, it’s clear that the blockchain ecosystem is still in its nascent stages. While decentralized protocols have reduced the cost of trust in transactions, the blockchain realm remains largely isolated from the rest of the world. A significant portion of the global economy has yet to reap the benefits offered by decentralized protocols.
The logical progression of public good staking involves funding and supporting initiatives aimed at expanding the entire multi-chain ecosystem. This approach allows every protocol to broaden its use cases and partake in the collective growth as the entire blockchain ecosystem advances.
To expand the overall ecosystem, blockchain protocols must forge connections with the real world. There are two ways to accomplish this: align with the past or integrate with the future. The past is already saturated and highly competitive. Why would individuals and institutions deeply entrenched in “TradFi” or “Web2” be willing to share their segments?
The only viable strategy to enlarge the ecosystem is to secure a stake in the future, and this future is anchored in the development and judicious application of frontier technologies.
Therefore, as we move forward towards the future of public good staking, we need to look for an arena with equal opportunities. where both hackers and established institutions are at the starting line together—founding startups at the frontier of knowledge and technology. Because hackers can do as much that established institutions can’t as those institutions can do that hackers can’t.
Why do most hackers currently work on software projects?
In the early 2010s, university hackathons began to surge in popularity, a trend significantly fueled by the evolution of open-source software and a flourishing Internet industry. The first impact of the hackathon movement was to allow people to build teams and learn software development outside universities. By collaboratively hacking innovative gadgets and developing new products, hackers could accelerate their learning far beyond the pace achievable within university settings. A testament to this phenomenon is the observable emergence of middle/high school students evolving into proficient hackers without undergoing formal computer science courses.
In fact, in the era of open source software, universities are terrible places to learn how to develop software, or transform an idea into a product.
Beyond fostering software development skills, hackathons fulfill a multitude of roles, ranging from talent recruitment for companies to the inception of startups. Identifying talent at a hackathon is substantially more straightforward than through exams or tests, allowing the most adept hackers to continue product development post-hackathon, potentially evolving these products into valuable startups.
The mid-2010s witnessed a further propulsion of the hackathon movement, driven by the swift advancement and adoption of blockchain technology. Unlike its predecessors, the blockchain tech stack is not only conducive to open-source development but also to monetization, thanks to the integration of protocol-native cryptocurrencies. This feature has significantly eased fundraising for open-source developers and hackers. Previously, acquiring investments required demonstrating exceptional business acumen; now, the threshold for hackers to establish startups has been markedly reduced.
The ability to build atop existing technology enables nascent, compact teams to create potentially impactful solutions. This is also a pivotal reason why contemporary hackathons and hacker communities predominantly concentrate on software.
The Hacker Movement is not a subset of the Open Source Movement
However, the core of the global hacker movement is not only the way people commit software code. It also encompasses the approaches to problem-solving, the processes of product development, and the creation of new technology platforms. The Hacker Movement fosters profound connections among hackers worldwide, eradicating geographical constraints, intertwining ideas, and enabling hackers to commence building without reliance on substantial institutions—they can simply begin to build.
While the open-source tech stack has indeed provided hackers with a solid foundation for building, the potential for creation extends far beyond the realm of software. Hackers, with their inherent problem-solving and innovative capabilities, can venture into diverse domains to build a myriad of solutions and products.
Open Platform Technology
Hackers can build new products based on open platform technologies. To be more clear here, an open platform technology is one that is not exclusive or restricted to a specific group of developers; it is accessible to a diverse range of people for development purposes.
Many public blockchains exemplify open-source and open platform technologies. Hackers can access their source code on GitHub and develop decentralized applications (Dapps) on top of these blockchains. However, it’s crucial to understand that open platform technology does not inherently equate to being open source.
However, it’s important to note that an open platform technology does not have to be open source.
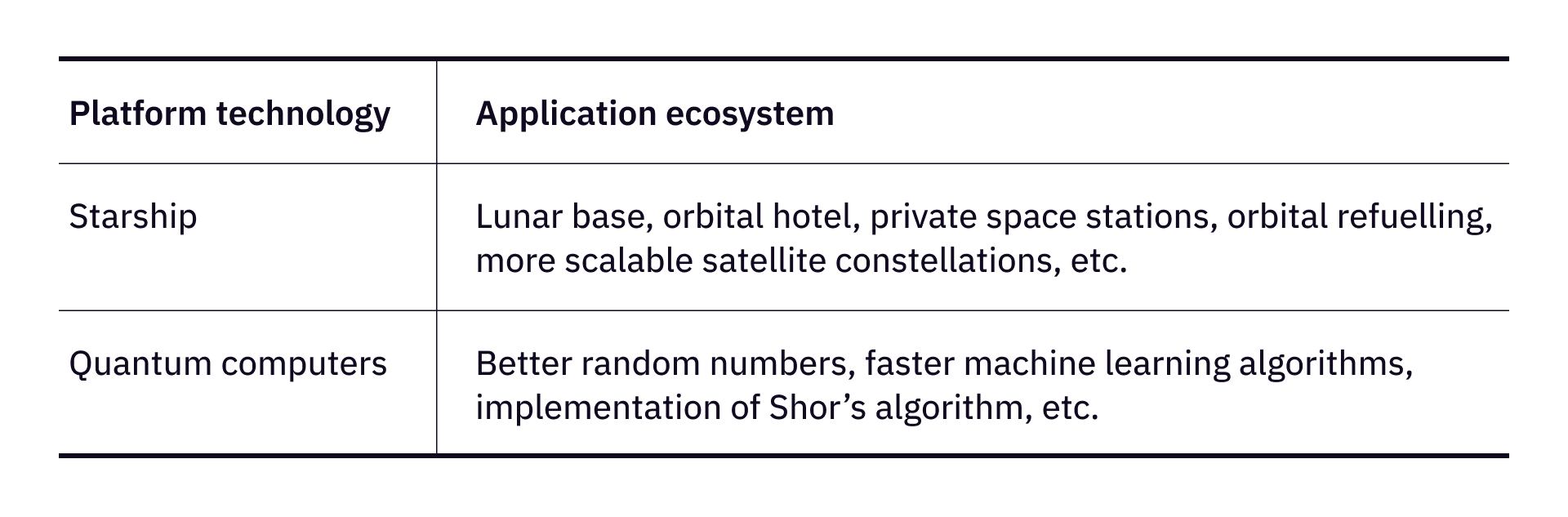
Starship, by SpaceX, can be categorized as an open platform technology, as it offers a universal platform for myriad developmental ideas, given its substantial volume and potentially reduced costs for space payloads. Generally, SpaceX does not impose restrictions on use cases or user demographics. Even if it does, alternative providers from varying jurisdictions would likely emerge, offering comparable technologies. For hackers, the design of payloads becomes a compelling endeavor, with well-conceived payloads potentially birthing successful startups.
Another example is quantum computers. The majority of quantum computing hardware is proprietary, akin to the Mac computer and operating system. However, hackers can develop useful algorithms and distinctive applications on quantum computers, facing considerably less competition than they would when developing for Mac or Windows.
The owner of a platform technology does not invariably dictate its applications and, more often than not, cannot monopolize its use cases. A company specializing in quantum computers may not necessarily offer the most prevalent algorithm on its platform, much like the most popular applications on the iPhone are not developed by Apple.
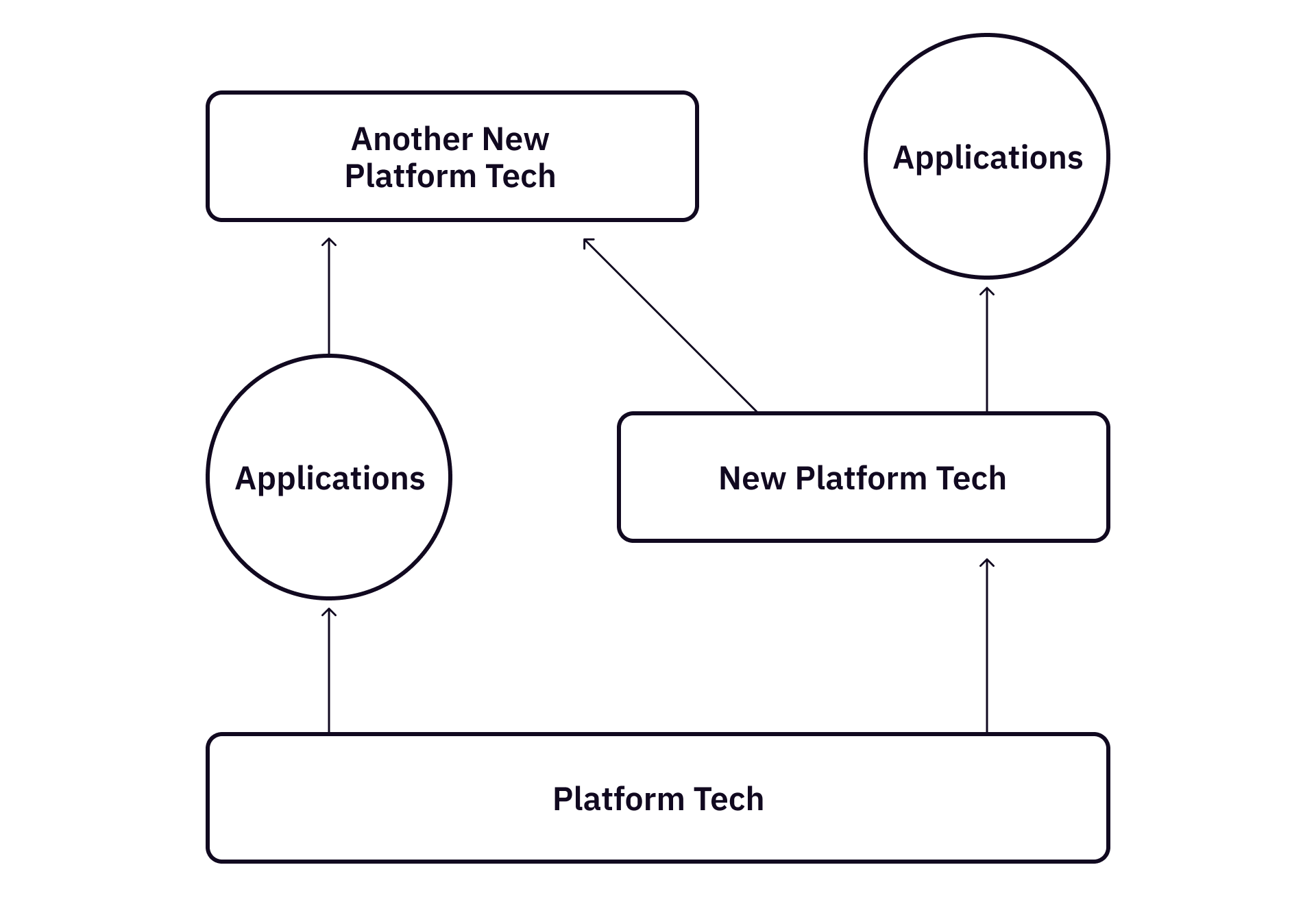
Can hackers build platform technologies? It depends. In the right circumstance, a young hacker can almost single-handedly start a new platform technology from some simple and novel ideas, like Google, Facebook, and Ethereum. However, we do not have to assume every hacker has to do so in order to build something important.
Developing platform technology often necessitates substantial capital and resources, particularly when it involves hardware and manufacturing. It’s not a prerequisite to assume that every hacker is equipped to develop a platform technology from scratch. Instead, hackers can swiftly develop groundbreaking applications with relatively minimal initial capital and resources, leveraging existing platform technologies.
Frontier Hackers are Underfunded
Currently, there is a noticeable disparity in funding and support for hackers working on frontier technologies. These individuals, who are at the cutting edge of innovation and exploration in fields like quantum computing, often face a lack of resources and financial backing compared to their counterparts in more established domains like blockchain.

Although a frontier tech company could raise more funding, they often have much bigger burn rate compared to software companies and blockchain companies. For example, Rigetti Computing currently holds roughly $100M cash at hand, but it can only support the company for 5 quarters given that their burn rate is around $20M per quarter.
On the other hand, a majority of Rigetti Computing’s revenue is from government and corporate contracts, given the ability of current quantum computers, it’s difficult for Rigetti to increase its revenue in 1-2 years, imposing great challenges for its survival.
Hacker Centric Roadmaps for Frontier Platform Technologies
While frontier platform technology provides opportunities for hackers to build cool products, the hacker community could redefine how these technologies are used.
Hackers building starship payload applications could greatly increase starship’s use. A successful company, originated from hacker innovation, could become a recurrent client for launch services from companies like SpaceX. Similarly, groundbreaking quantum software could generate substantial revenue for quantum computing hardware providers, much like how a great decentralized protocol could benefit its underlying public blockchain by paying gas fees.
A hacker centric roadmap to the development of open platform technologies offers a dynamic and agile alternative for the exploration and realization of novel use cases. A single successful innovation emanating from the hacker community can not only bring substantial revenue to the platform but also act as a catalyst, inspiring more hackers to build upon it. This creates a self-reinforcing cycle, fostering a thriving ecosystem of innovation and startups. Such a vibrant ecosystem fuels optimism and interest in the technology, drawing more hackers and innovators to contribute.
By embracing the “hacker movement,” platform technologies can diversify their reliance on revenue streams, reducing dependence on government contracts and fostering a dynamic and resilient ecosystem. This approach not only generates a spectrum of possibilities and hope but also establishes a robust and self-sustaining environment of continuous innovation and development—lessons that frontier tech companies can certainly glean from their counterparts in the blockchain sector.
“Frontier Staking” - Bootstrap and Sustain Frontier Hacker Communities
Public Good Staking can indeed serve as a transformative conduit, bridging the blockchain and frontier technology realms by channeling sustained funding to frontier hacker communities. The bootstrap of a frontier hacker community can start with funding frontier hackathons and grant programs such as the Space Resources and Explorations Grant and the NISQ Quantum Computing Grant, then automate the process by using DoraHacks.io and Dora Factory tools.
In the majority of scenarios, hackers are likely to develop application-level products leveraging specific platform technologies, or solve specific technical problems with frontier technology. A consistent flow of resources from the Public Good Staking reserve can empower a number of frontier hacker communities and frontier BUIDL teams.
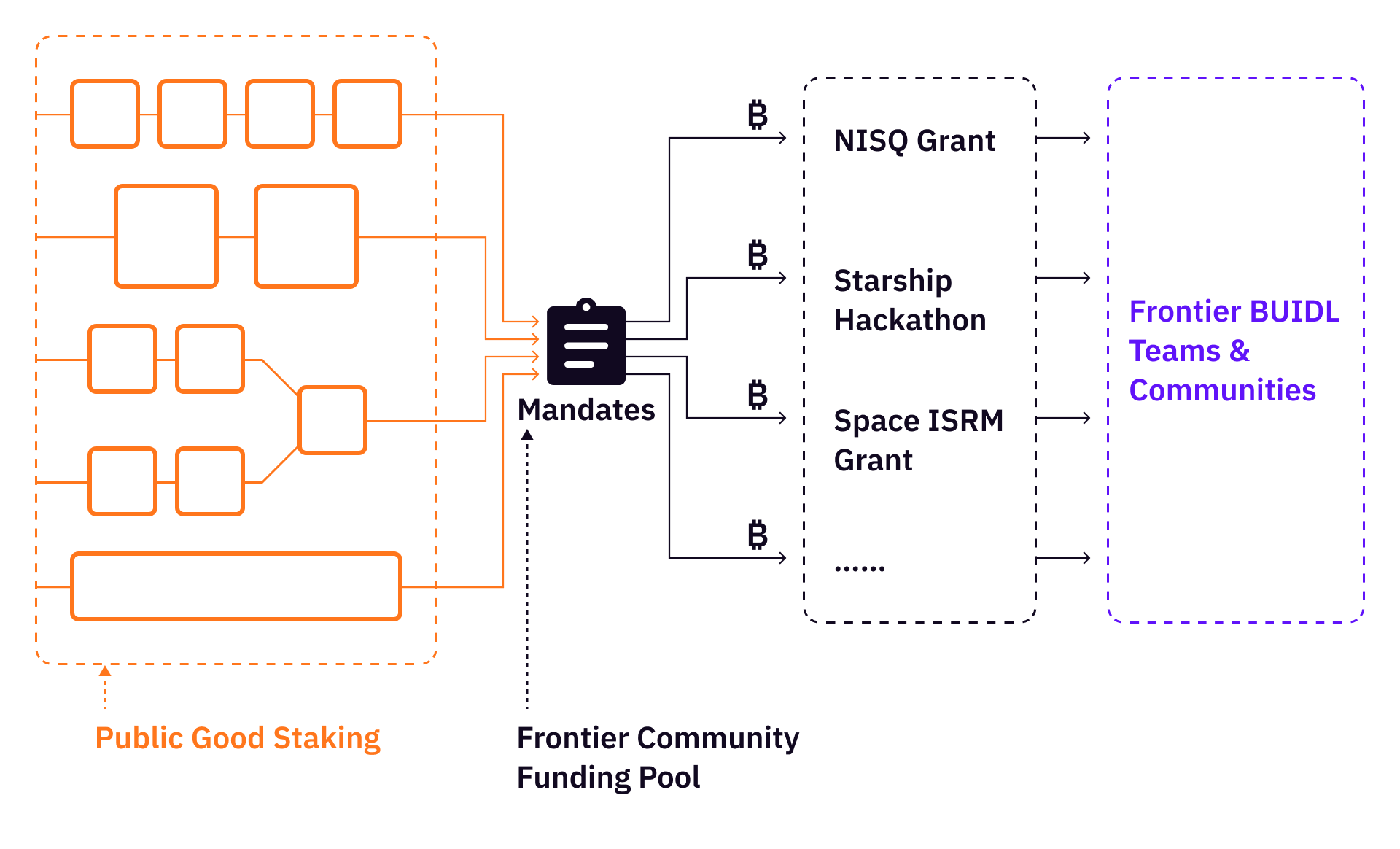
Over time, the continued growth of a frontier hacker community will create a sufficient number of productive use cases for the community to make sense. If we keep doing this for enough time, the frontier hacker community will eventually be able to become self-sustainable. A self-sustainable frontier hacker community can bring forth the following:
- Creating opportunities: It can open up a myriad of opportunities for hackers interested in developing products powered by frontier technologies, allowing them to delve into uncharted territories and innovate in areas that are at the cutting edge of technology;
- Transforming Development Approaches: Transform the developmental strategies of many frontier tech companies by fostering the creation of robust hacker communities and ecosystems centered around the technology. This approach can facilitate collaborative innovation and contribute to the holistic development and advancement of the technology;
- Bridging worlds: build a dynamic link between the blockchain realm and the future landscape of productivity, creating a synergistic environment where the principles and technologies from both domains can converge to generate groundbreaking solutions and advancements.
Used ChatGPT to fix grammar & polish languages for this article.